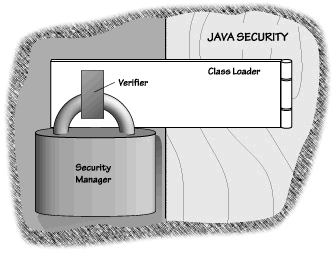
In addition to many safety-related characteristics of the Java language, Java security relies on a multipart defense. The default sandbox is made of three interrelated parts: the Verifier, the Class Loader, and the Security Manager. In the early days (way back in 1996), people often referred to the Java security model as a "three-layer" defense. Though such a label is still encountered at times in the Java security literature, it is misleading. The layer terminology implies that if an applet penetrates the first "layer," two layers are left to set things straight. Actually, the parts are more like links in a chain: If any of the three parts breaks, the entire security system breaks. Figure 2.2 emphasizes that for the security model to work, each of its parts must work perfectly.
With the introduction of JDK 1.1 and Java 2, the Java security model was extended to include more parts. First came the java.security package. This package is an API that includes both a cryptographic provider interface (by which different cryptography implementations can be added into Java) and APIs for common cryptographic algorithms. (These are sometimes called the "security" classes, though this is a misnomer. Security consists of much more than just cryptography.) It is this functionality that allows the VM to authenticate signed Java classes. Another part, the Access Controller, was introduced with JDK 1.1 and significantly enhanced with Java 2. We learn more about the security package and the Access Controller in Chapter 3. The next three sections are each devoted to one part of the base security model: the Verifier, the Class Loader, and the Security Manager. Each of these parts depends in some way on the others. For the security model to function properly, each part must do its job flawlessly, and the parts must fit together perfectly. Between them, the three parts perform load time and runtime checks in order to restrict file system and network access (as well as restricting access to browser internals).

Chapter... Preface -- 1 -- 2 -- 3 -- 4 -- 5 -- 6 -- 7 -- 8 -- 9 -- A -- B -- C -- Refs
Copyright ©1999 Gary McGraw and Edward Felten. |