Many Net-savvy people are aware of a simple trick that allows users to forge electronic mail. This is accomplished by talking directly to the SMTP daemon on port 25 of a server machine. The mail-forging attack takes advantage of the fact that mail-serving hosts monitor port 25 for incoming Simple Mail Transfer Protocol (SMTP) messages. One of the Internet rites of passage is to telnet to port 25 and send fake mail to a friend. This game is very well known; however, the scheme is easily debunked. The SMTP daemon actually marks the forged mail with the IP number of the machine that connected to port 25, which makes it very easy to discern which machine sent the mail.3 Spammers often forge mail headers so that the true source of a spam message is hard to discern. It is usually easy to detect forged mail by looking carefully at the header. The machine listed in the From line should be the same as the Received: line. Most users and mail readers look only at the From line; systems people know to look at both. Note that some legitimate mail may have differing From and Received: lines, depending on how people send their mail. Here is an example of mail forged by an author on his home machine (tigger.mediasoft.net) to his own work account. Note how the From and Received: lines differ.
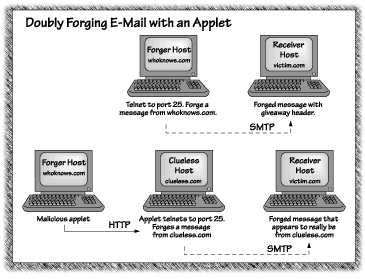
Applets provide an interesting new twist on the standard approach to mail forging. Because applets load across the network and run on a Web surfer's machine, a mail forging applet can cause the standard SMTP daemon monitoring port 25 to report mail coming from the Web surfer's machine-not the machine serving the applet. This can be leveraged to doubly forge mail. Imagine that Alice hits a Web page and an applet is consequently run on her machine. By using Alice's machine to forge mail from Alice-that is, to forge mail apparently both from her machine and from her account on that machine-the doubly forged mail appears not to have been forged at all! With many standard server configurations, this forging attack is possible. Figure 4.4 illustrates the difference between the standard port 25 attack and the revised applet attack.
Forged mail of this sort can be sent to any email address that the applet's author chooses. The message could, of course, be anything at all. To make this more concrete, imagine an applet that sends an email death threat to the president of the United States (a felony) from the account and machine of anyone na´ve enough to browse a malicious Web page with Java enabled. Or, imagine an applet that uses mail to spam hundreds of Usenet newsgroups with a fake legal advertisement apparently posted from the victim's machine and account, immediately spawning a mail bomb attack against the applet's victim from angry Usenet users bent on retaliation. There are many variations on this theme. Using threads, it is possible to forge mail in the background while doing something seemingly innocuous in the foreground. This forging activity is currently possible; in fact, there are multiple examples to be found on the Web. The possibly surprising fact is that the attack we have described is completely within the security bounds of what SMTP and Java are allowed to do. Forging mail like this is neither particularly sophisticated nor hard to implement. On the other hand, the havoc that could be wreaked with a malicious applet of this sort is serious.

Chapter... Preface -- 1 -- 2 -- 3 -- 4 -- 5 -- 6 -- 7 -- 8 -- 9 -- A -- B -- C -- Refs
Copyright ©1999 Gary McGraw and Edward Felten. |